Think beyond door control
Controlling the primary entrances and exits at your business is always a critical starting point in physical security and access control. It begins with the proper locking devices on the door itself and migrates to the latest technology for added security.
Access control technologies are a mainstay of professionally installed systems and they never take a one-size-fits-all approach. Every security specification needs to be individually tailored to the user, the facility and the nature of the operations. A number of different factors include through-put, which is the number of people who are using the system, as well as the environment itself, including weather or even installation or wiring constraints. At Hoosier Security, customization to meet your needs is how we begin the process. We don’t lead with technology or equipment, because each solution is individually tailored to meet the specific physical security requirements of the customer.
There are many different possible options for access control. Some businesses may do well with simple magnetic stripe card functionality, which is cost-effective yet highly secure. Others may require hands-free devices, also called proximity, with can be used from a short distance and do not require to be inserted into a card reader. There are also longer-range access control devices which are wireless and can be used in parking garages or gated communities to open gates or other barriers at even longer distances.
For those ultra-secure areas – data centers, computer labs or pharmaceutical storage – biometrics which use fingerprint or hand scan technologies may also be in order. Biometrics have dropped in price, making them a possible alternative for high-risk or high capital areas of the business or even selectively used at a single door at the business.
Managing your access control solution has become easier and more flexible with the advent of cloud-hosted technologies. Hoosier Security offers many different ‘flavors’ of the latest cloud-based access control. These software programs can be controlled by the user who wants to handle all the administration of the specification, such as issuing cards or fobs and setting schedules, or we can handle all of these tasks or certain parts which may alleviate some work load. It’s up to you. Best of all, cloud-hosted programs receive automatic updates to the latest versions so customers can be assured they are working with the most up-to-date software available.
Consider all the possibilities
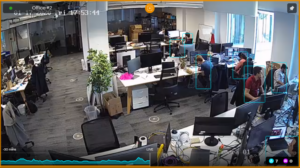
Access control today extends beyond physical security. It can be teamed or integrated with surveillance cameras to ascertain who might be trying to gain access, or perhaps has been denied access, with real-time visual information. It’s also great for human resources to track when employees clocked in or out of the business, or if someone gained access to the facility after hours, perhaps after inventory was missing. That makes it perfect for warehouse operations and overall business accountability. It can be used in fleet management as well. A wireless reader can allow an employee to use a forklift or other equipment – but only after they have completed necessary certification or other training required. In this way, their credentials are programmed to allow or deny access, depending on the status.
The right solution doesn’t start with product. The correct process, as followed by Hoosier Security, is to assess the security, evaluate challenges and custom-design the system that addresses issues and challenges as succinctly as possible. Contact us today at 317-644-0570 for a free consultation.